Wireless Security - Tools
Correct implementation of the security controls in wireless networks is critical nowadays, since it directly affects the profitability of some businesses and information confidentiality. Wireless security tools, should be used to test (audit) wireless implementations regularly. Good wireless security audit is not only practical testing, but also proper documentation, including recommendations of how to make WLAN more secure.
There is a bunch of possible audits, one can try to perform −
- Layer 1 Audit
- Layer 2 Audit
- WLAN Security Audit
- Wired Infrastructure Audit
- Social Engineering Audit
- Wireless Intrusion Prevention System (WIPS) Audit
Wi-Fi Security Auditing Tool
In the previous part, we listed a set of audits that can be carried out, in order to assess the security of the wireless implementation. We will try to go through the points one by one and see – firstly, why a particular audit is relevant and secondly, how one can perform it.
Layer 1 and Layer 2 Audit
The goal of a Layer 1 Audit is to determine the RF coverage (part of performance-based site survey) and find out about potential sources of RF interferences (part of the security audit for identification of sources of Layer 1 DoS). During a Wireless Security Audit, one conducts spectrum analysis to detect any continuous transmitters or intentionally put RF jammers (that causes a Layer 1 DoS).
As for a Layer 2 Wireless Audit, the goal is to detect any rogue devices or unauthorized 802.11 devices. Performing a Layer 2 Audit is critical in environments, that do not have a Wireless IPS (WIPS) monitoring deployed (otherwise WIPS will do that work automatically, since this is its job).
A list of points that the auditor should concentrate on, while performing layer 2 site survey is: MAC addresses, SSIDs, types of devices being used, types of traffic, channels that are in use, possible default configurations, possible layer 2 attacks taking place, ad-hoc clients, etc.
While performing layer 1 or layer 2 audit, the auditor might use the following tools −
Protocol sniffers/analyzers (ex. Wireshark)
2.4/5 GHz signal injectors.
Offensive tools (mdk3, Void11, Bugtraq, IKEcrack, FakeAP, etc.)
As an example I will show you a Swiss-army knife tool called mdk3. It is a proof-of-concept tool that allows for exploiting wireless network. Just to name few options, it allows you to do −
Flood fake beacon tools (as a way to imitate a fake AP).
DoS of authentication frames (may lead to AP's freeze or restart if vulnerable).
Flood of disassociation/de-authentication frames (to kick out valid users out from the network).
802.1X wireless security testing.
Abusing Wireless Intrusion Prevention/Detection Systems (WIPS/WIDS) and bunch of other harmful things.

Creation of the Layer 2 DoS of de-authentication frames using your kali Linux (mdk3 tool) is extremely simple and may be achieved with a single command, as shown in the following screenshot.

Of course, there is always a bunch of ways of getting the same result. You can get the same effect using aireplay-ng tool. The MAC address after "-a" is the BSSID value of the AP that broadcasts particular WLAN network.

WLAN Security Audit
The goal of WLAN security audit is to investigate if and how a particular WLAN may be compromised. The types of weaknesses, the potential attacker would look for (and weaknesses that wireless security auditor should concentrate on) are mainly related to authentication, encryption, types of the deployed WLANs, weak keys in use and similar.
The tools that are a good match for that use are −
Protocol sniffers/analyzers (ex. Wireshark).
Wireless discovery tools (ex. NetStumbler, Kismet, Win Sniffer, WiFiFoFum, etc.).
Encryption/Authentication breaking (testing) tools (aircrack-ng, custom scripts, all kinds of cryptoanalysis tools).

As you can see, the basic WLAN security audit is not something you need a specialized software for. Using the app on your smartphone might do the work!
Wired Infrastructure Audit
With respect to the wireless network communication, it's wired part also needs to be secured in order for the whole system to be considered safe. Wired infrastructure audit should cover the following pointers −
- Inspection of the firewall used to restrict WLAN user access to certain network resources.
- Switchport interfaces that are unused should be disabled.
- A strong password should be used, and protocols with built-in encryption should be used (HTTPS, SSH), if possible.
Social Engineering Audit
Social Engineering is the type of "attack" that uses non-technical approaches to get the information. Instead of trying to crack the wireless password, maybe it's easier to ask for it? Maybe it would be easier to get the WPS PIN, that would allow you to connect to protected WLAN?
Those scenarios sound amazing, but I can assure you, that they happen in real life too. In order to protect against it, the most important thing is to be aware of what data should be kept private and what to be shared. In home environments where you are the "admin" of the network, it is only you who can decide what should be kept private. On the other hand, in enterprise environments, it would be a role of security departments to issue security awareness campaigns to educate personnel, of what would be a right use of the wireless network and what would be a misuse.
Wireless Intrusion Prevention Systems
On the wired network, the Intrusion Prevention System (IPS) is used to perform deep packet inspection of the traversing packets, in order to look for anomalies, Trojans or other malicious pieces of code.
In the wireless world, it is similar, however focuses on reacting to rogue wireless devices, rather than security events. Wireless Intrusion Prevention System (WIPS), concentrates on detecting and preventing the usage of unauthorized wireless devices. The whole idea behind WIPS, is to have some APs in your infrastructure dedicated configured in WIPS mode (do not broadcast any WLAN network or allow user to associate). Those AP's are preconfigured for a particular frequency channel and they just listen to the frequency spectrum all the time, looking for anomalies.
Another approach is to have a set of dedicated passive sensors (instead of APs) to perform this job. The different type of anomalies, that you may expect to see are: flood of de-authentication frames, or flood of disassociation frames, detecting WLANs broadcasted by AP's with unknown BSSID, etc. If you think of deep packet inspection or malicious code detection, they still need to be detected on the wired network, using dedicated IPS/IDS devices.
You as an attacker have no means to run a WIPS solution as it is a defensive technical measure. Due to its price and management overhead, only bigger enterprises may have it running (still it's quite rare). One of the possible deployments of WIPS solution, can be based on the Cisco Wireless Infrastructure model. The Cisco Wireless solution (in its simplest form) is based on the Wireless LAN Controller (WLC) and set of APs. WIPS solution, would assume that some AP’s are taken out of regular WLAN service, and are set to IPS mode, and dedicated purely to inspect the frequency spectrum.
The main page of the Cisco Wireless LAN Controller (WLC) is shown below (confidential fields were covered with the circle filled with black).

This particular WLC is currently managing 38 AP’s that has joined it. Detailed list of all the AP's, together with its MAC addresses, IP addresses and the AP mode, may be viewed under the "Wireless" tab.

All of the AP's that are currently joined, they are set in "Local Mode". It means that they are dedicated to provide regular wireless coverage, and announce all the configured WLANs. In order to transform particular AP into "IPS mode" as we know it, we need to click on one of the AP's and change its "AP mode" to special "monitor mode".
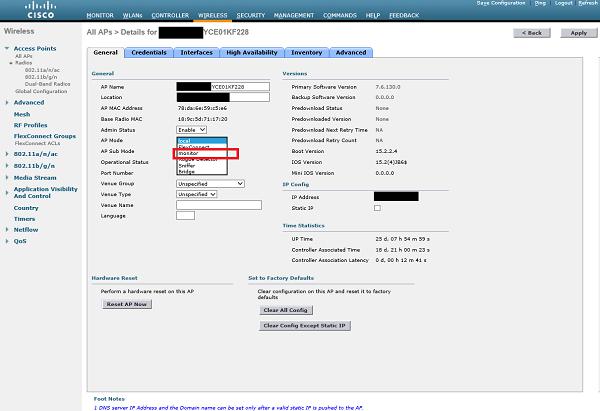
After the AP is set in "Monitor" mode and the change is applied, AP will restart. From that point, its only work is to listen on the frequency spectrum, and detect wireless-side attacks. By default, WLC has predefined set of signatures that AP will look for. They are listed in the following screenshot −

As you can see, the item number 9 is "Deauth flood", with Frame Type - Management and corresponding Action - Report (it means that it will only notify about the attack using log messages, but will not take any action).
With the setup as we have here, when potential attacker would use mdk3 or aireplay-ng tool to interfere with the existing WLAN network, based on Cisco Wireless Infrastructure - the attack will be detected and network administrators will be notified. There are other products that may take wireless security to the next level. With wireless tracking services, the tool may detect your exact geographical location in some very secure locations, maybe a guard would come to inspect the source of the attack, or police may be called.
As I mentioned earlier, you can meet such a setup only in enterprise environments. In smaller deployments or home environments, you would not meet such security measures.










