Pentesting WPA/WPA2 Encrypted WLAN
WPA/WPA2 is the next evolution of secure wireless network that came up after WEP turned out to be insecure. The algorithms used by those protocols are much more secure (WPA: TKIP and WPA2: CCMP/AES), making it impossible to crack the network, using the same approach we did with WEP.
Breaking of WPA/WPA2 is based on the same idea – sniffing the initial 4-way handshake and applying brute-force attack in order to break encrypted password.
To illustrate this example, I will once again make use of the "LAB-test" WLAN, this time secured with WPA2 using the following key− " F8BE4A2C". As you remember from the previous chapters, success and time required from brute-forcing of the password depends on the complexity of password. The password, I have used here is potentially weak-enough to be crack-able in a relatively reasonable time. In real-environments you should only see the password, that are 10+ characters long and have all types of alphanumeric signs included – that way, it would take years to brute-force it.
The same as in last example, we will start with airodump-ng, to passively collect some information about the WLAN.

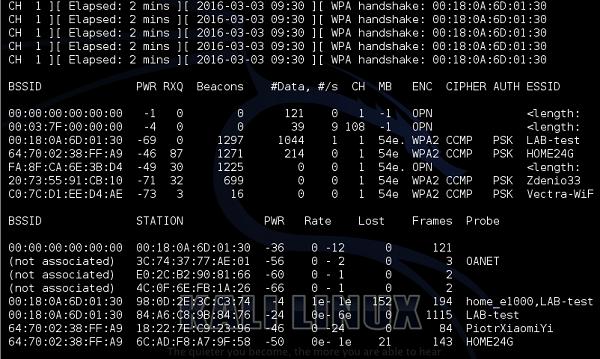
As you can observe, indeed he have "LAB-test" SSID secured with WPA2 with CCMP encryption. The client connected to LAB-test is currently my other PC with MAC address of 84: A6:C8:9B: 84:76.

First step is to enable sniffing of the traffic on (we don't care that much about data packets this time) LAB-test is order to collect the initial 4-way handshake between AP and Wireless Client (my PC).

As you can see below, every time a new user joins the network, airodump is sniffing the 4-way handshake.
As we have those handshakes collected in a file, we are ready to crack the password. The only missing element is a dictionary file with possible passwords. There is bunch of tools you can use like john, crunch or you can even download the dictionary file from the internet. In this example, I will show crunch, but feel free to experiment with all the solutions you may find. Remember, the sky is the limit.

As you can see, crunch can create a dictionary for you. Let's assume that we want to have all passwords with number and letters up to 8 characters in length. And let's assume that the number may be from 0 to 9 and letters from A to F. Why we make this limitations (assumption about the password)? – it is because, if you want to have a file with all the combinations of password composed of number 0-9, letters a-z and A-Z, you need a space of 18566719 GB (!!!).
So first we create all the combinations and put them in a dictionary file.

Then, we reference this dictionary file in using the aircrack utility to try to derive the right key, as follows −

The aircrack-ng has found 8 BSSID's in the file, therefore it asks you – which is the WLAN you want to crack – I referenced number 2 – "LAB-test" network.
Checking each of the passwords, in one-by-one fashion is a very long process. The time to find a right password depends on how far in a dictionary file the password is put (If you are lucky, you can find the password in your first guess, if the password is put in 1st line of the dictionary file). In this example, as you can see, I have found the password, but it took 8 hours and 47 minutes (!!!). Using a password of 10 characters instead of 8 would increase the time probably to days or maybe week.

You have to keep in mind, that the longer the dictionary, the longer it will take to break the password. And, as I underlined a few times earlier, if the password is pretty complex and long, it is computationally not feasible to perform cracking at all (in the limited time, let's say under 10 years).










