CICS - Nucleus
The five CICS system components described earlier are a convenient grouping of CICS system programs, each of which performs its own specialized functions. The core of CICS known as the CICS Nucleus which consists of IBM-supplied CICS Control Programs and Control Tables.
Control Programs
CICS nucleus is constructed by the control programs and corresponding control tables. It provides unique advantages. It makes the CICS system highly flexible and thus easy to maintain. Following are the important control programs of CICS −
TCP
TCP is known as Terminal Control Program.
TCP is used to receive messages from the terminal.
It maintains hardware communication requirements.
It requests CICS to initiate the tasks.
KCP
KCP is known as Task Control Program.
PCP
PCP is known as Program Control Program.
PCP is used to locate and load programs for execution.
It transfers the control between programs and in the end, it returns the control back to the CICS.
FCP
FCP is known as File Control Program.
FCP is used to provide application programs with services like read, insert, update or delete records in a file.
It keeps exclusive control over the records in order to maintain data integrity during record updates.
SCP
SCP is known as Storage Control Program. It is used to control allocation and deallocation of storage within a CICS region.
Control Tables
CICS consists of IBM-supplied CICS control programs and tables. These tables need to be updated accordingly with the application information for successful execution of CICS application programs. Following are the important Control Tables −
TCT
TCT is known as Terminal Control Table.
When we login to a CICS terminal, an entry is made in the TCT table.
TCT contains the terminal ID's that are connected to current CICS region.
Terminal Control Program along with terminal control table recognize the incoming data from the terminal.
PCT
PCT is known as Program Control Table.
PPT
PPT is known as Processing Program Table. PPT contains Program name or Mapset name, Task Use Counter, Language, Size, Main storage address, Load library address, etc.
Program or Mapset name is unique in a PPT table.
CICS receives the transaction and a corresponding program name is allocated to the transaction from the PCT. It checks if the program is loaded or not. If it is loaded, then the task use counter is increased by 1. If the program is not loaded, then the program is first loaded and the task use counter is set to 1. It gets the load library address from the PPT table.
FCT
FCT is known as File Control Table.
It contains File names, File type, record length, etc.
All the files used in a CICS program must be declared in FCT and they are opened and closed by CICS itself.
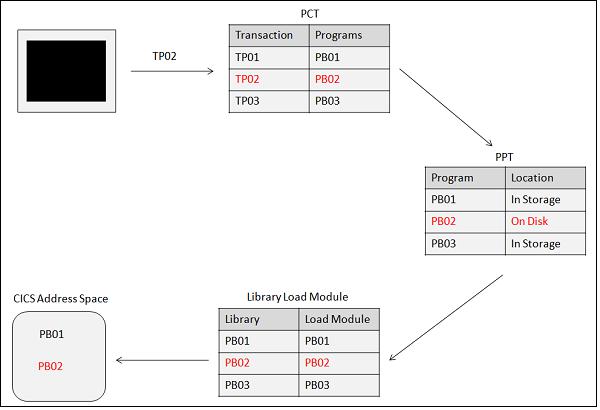
Transaction
When a transaction identifier TP02 is entered on the CICS terminal, first it checks if there is a program associated with this Transaction identifier in the PCT table. If it finds one, then it checks in the PPT table to find the location of the Program to execute it.
If the program is already available in the memory, it starts executing that particular program; if not, it loads the program to the memory from the secondary storage and then starts executing it.
Transaction Life Cycle
The transaction life cycle has the following steps −
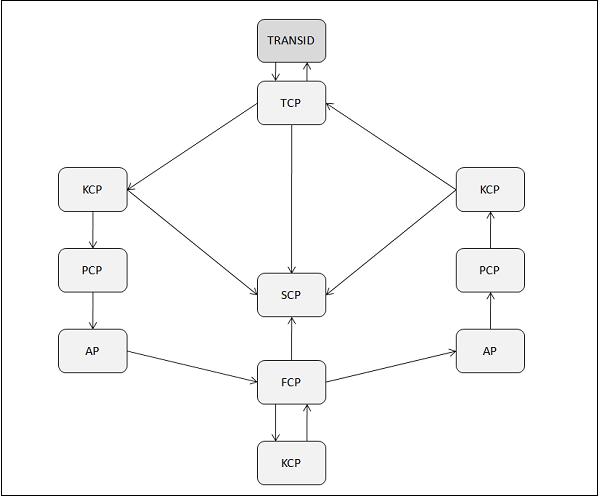
Step 1
The terminal operator initiates the transaction by typing a 1 to 4 character transaction-id and pressing the ENTER key.
Step 2
The TCP periodically checks all the terminals for input. When a message is received, it does the following −
Instructs the SCP to create a TIOA.
Places the message in the TIOA.
Passes the control to the KCP.
Step 3
The KCP takes control from the TCP and does the following −
Validates the transaction-id and security.
Instructs the SCP to create a task control area.
Assigns priority to the task based on Terminal priority (Set in TCT), Operator priority (Set in SNT), and Transaction priority (Set in PCT).
Adds the task to the queue of waiting programs.
Dispatches waiting programs in the order of priority.
Passes the control to the PCP.
Step 4
The PCP takes control from the KCP and does the following −
Step 5
The Application program takes control from the PCP and does the following −
Step 6
The FCP takes control from the Application program and does the following −
Step 7
The KCP does the following −
Dispatches the next task in the queue.
Re-dispatches the old task when I/O is complete.
Transfers the control to the FCP.
Step 8
The FCP returns control to the Application program.
Step 9
The Application program does the following −
Step 10
The PCP returns the control back to the KCP requesting it to end the task.
Step 11
The KCP instructs the SCP to free all the storage allocated to the task (except TIOA).
Step 12
The TCP does the following −




